0ae373bc1e9afb5d6463cf937a339b10b5376260
* web: Add InvalidationFlow to Radius Provider dialogues
## What
- Bugfix: adds the InvalidationFlow to the Radius Provider dialogues
- Repairs: `{"invalidation_flow":["This field is required."]}` message, which was *not* propagated
to the Notification.
- Nitpick: Pretties `?foo=${true}` expressions: `s/\?([^=]+)=\$\{true\}/\1/`
## Note
Yes, I know I'm going to have to do more magic when we harmonize the forms, and no, I didn't add the
Property Mappings to the wizard, and yes, I know I'm going to have pain with the *new* version of
the wizard. But this is a serious bug; you can't make Radius servers with *either* of the current
dialogues at the moment.
* This (temporary) change is needed to prevent the unit tests from failing.
\# What
\# Why
\# How
\# Designs
\# Test Steps
\# Other Notes
* Revert "This (temporary) change is needed to prevent the unit tests from failing."
This reverts commit dddde09be5.
* web: Make using the wizard the default for new applications
# What
1. I removed the "Wizard Hint" bar and migrated the "Create With Wizard" button down to the default
position as "Create With Provider," moving the "Create" button to a secondary position.
Primary coloring has been kept for both.
2. Added an alert to the "Create" legacy dialog:
> Using this form will only create an Application. In order to authenticate with the application,
> you will have to manually pair it with a Provider.
3. Updated the subtitle on the Wizard dialog:
``` diff
- wizardDescription = msg("Create a new application");
+ wizardDescription = msg("Create a new application and configure a provider for it.");
```
4. Updated the User page so that, if the User is-a Administrator and the number of Applications in
the system is zero, the user will be invited to create a new Application using the Wizard rather
than the legacy Form:
```diff
renderNewAppButton() {
const href = paramURL("/core/applications", {
- createForm: true,
+ createWizard: true,
});
```
5. Fixed a bug where, on initial render, if the `this.brand` field was not available, an error would
appear in the console. The effects were usually harmless, as brand information came quickly and
filled in before the user could notice, but it looked bad in the debugger.
6. Fixed a bug in testing where the wizard page "Configure Policy Bindings" had been changed to
"Configure Policy/User/Group Binding".
# Testing
Since the wizard OUID didn't change (`data-ouia-component-id="start-application-wizard"`), the E2E
tests for "Application Wizard" completed without any substantial changes to the routine or to the
tests.
``` sh
npm run test:e2e:watch -- --spec ./tests/specs/new-application-by-wizard.ts
```
# User documentation changes required.
These changes were made at the request of docs, as an initial draft to show how the page looks with
the Application Wizard as he default tool for creating new Applications.
# Developer documentation changes required.
None.
core: revert bump oss/go/microsoft/golang from 1.23-fips-bookworm to 1.24-fips-bookworm (#13012) (#13022)
core: revert bump oss/go/microsoft/golang from 1.23-fips-bookworm to 1.24-fips-bookworm (#13012) (#13022)
core: revert bump oss/go/microsoft/golang from 1.23-fips-bookworm to 1.24-fips-bookworm (#13012) (#13022)
core: revert bump oss/go/microsoft/golang from 1.23-fips-bookworm to 1.24-fips-bookworm (#13012) (#13022)
core: revert bump oss/go/microsoft/golang from 1.23-fips-bookworm to 1.24-fips-bookworm (#13012) (#13022)
What is authentik?
authentik is an open-source Identity Provider that emphasizes flexibility and versatility, with support for a wide set of protocols.
Our enterprise offer can also be used as a self-hosted replacement for large-scale deployments of Okta/Auth0, Entra ID, Ping Identity, or other legacy IdPs for employees and B2B2C use.
Installation
For small/test setups it is recommended to use Docker Compose; refer to the documentation.
For bigger setups, there is a Helm Chart here. This is documented here.
Screenshots
| Light | Dark |
|---|---|
 |
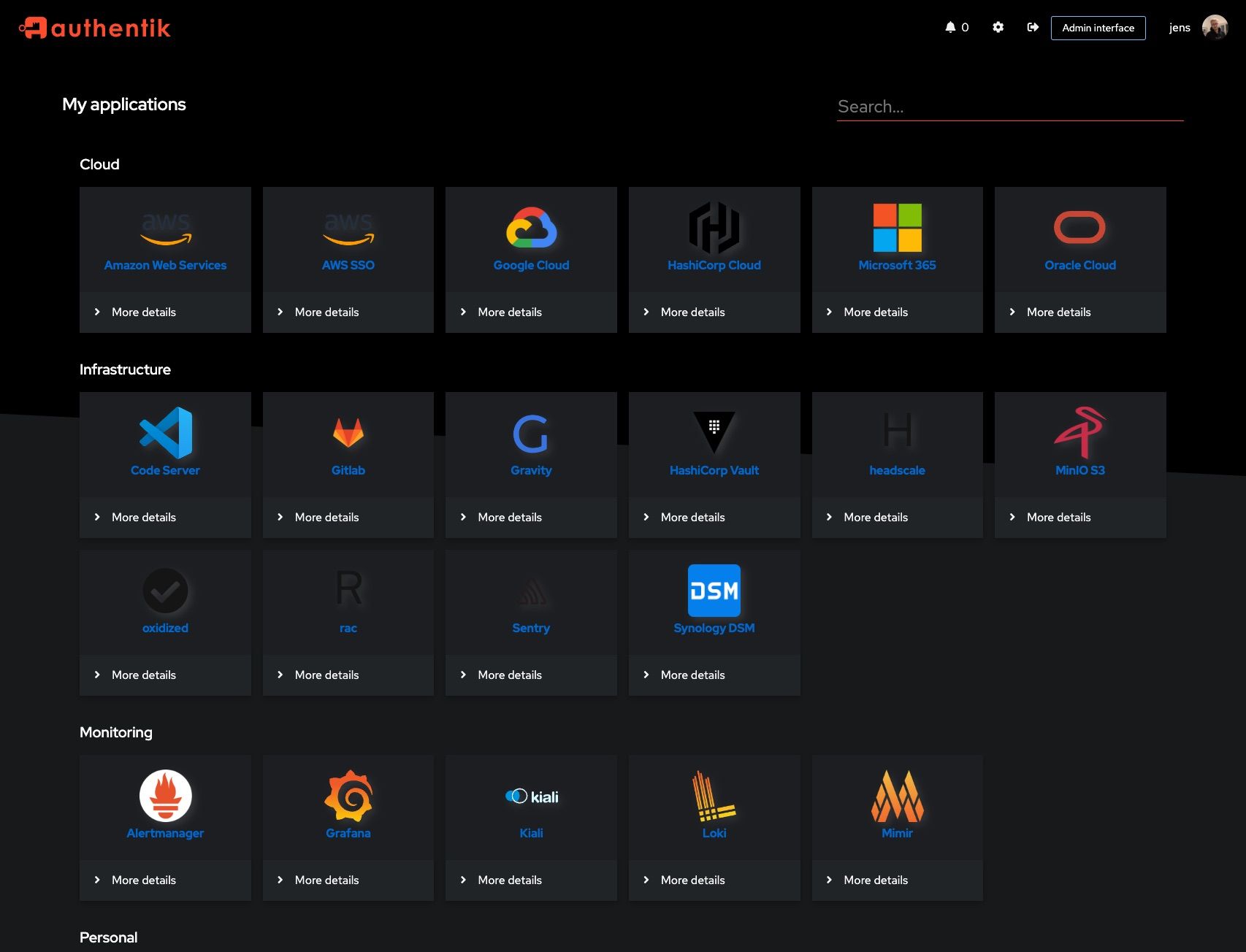 |
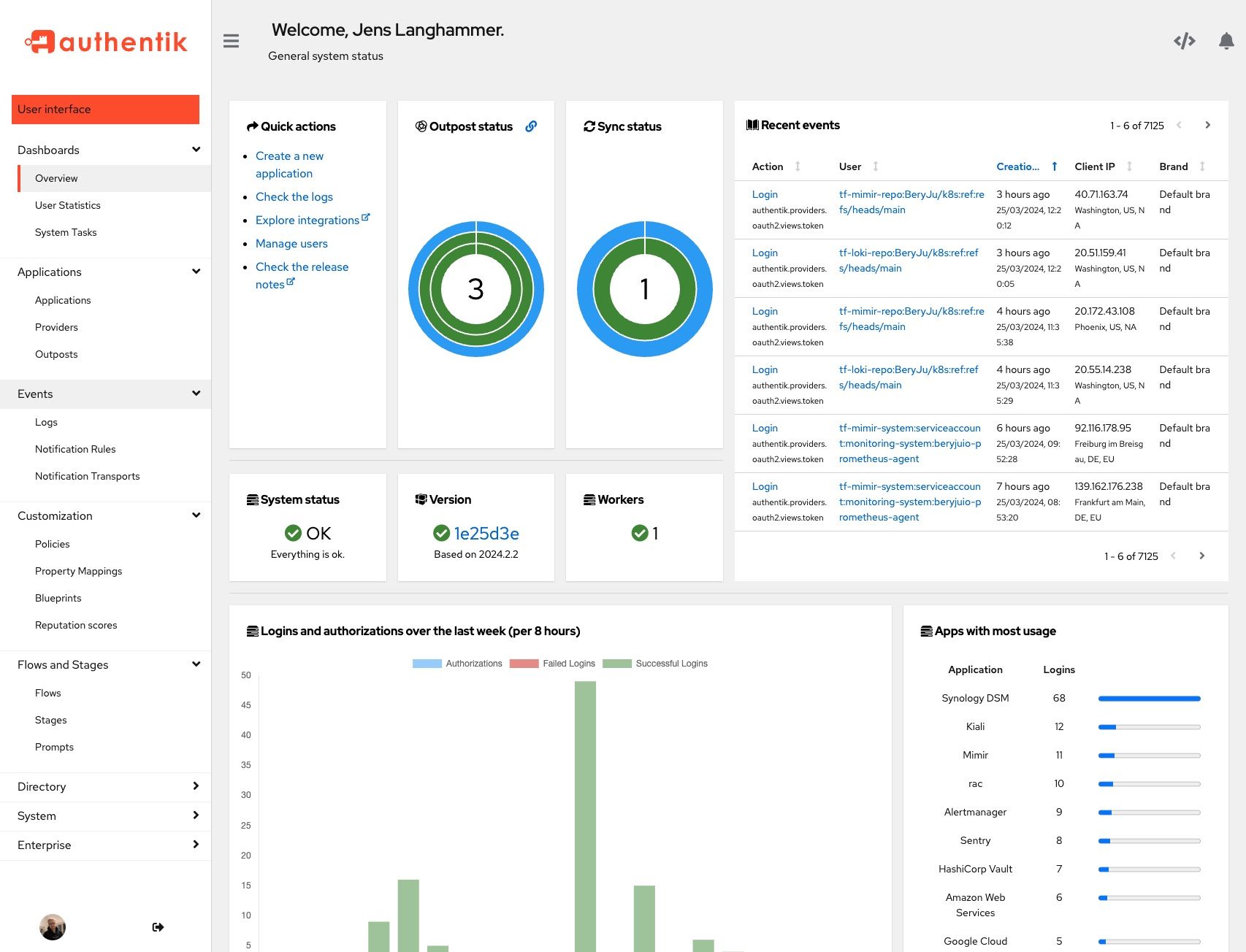 |
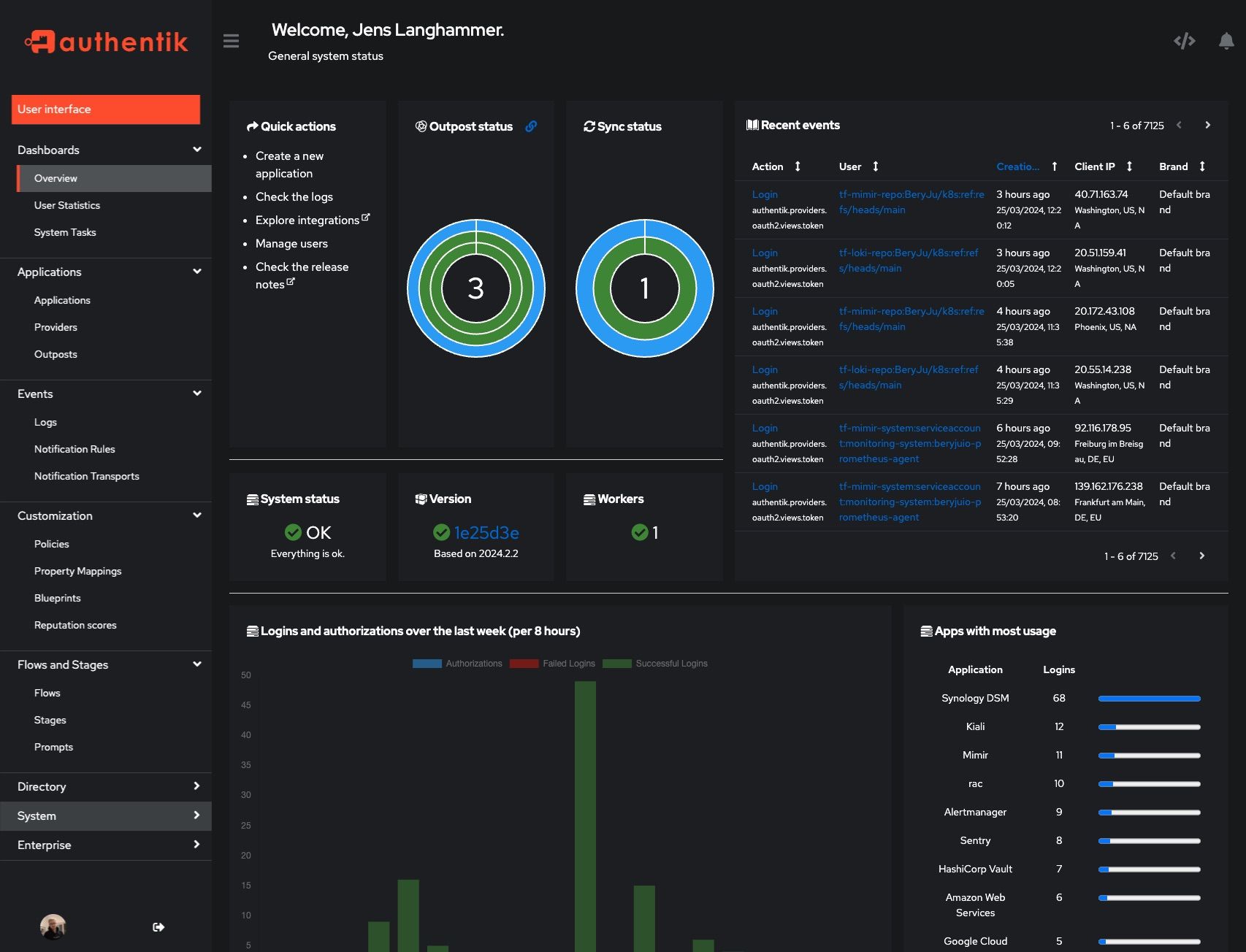 |
Development
Security
See SECURITY.md
Adoption and Contributions
Your organization uses authentik? We'd love to add your logo to the readme and our website! Email us @ hello@goauthentik.io or open a GitHub Issue/PR! For more information on how to contribute to authentik, please refer to our CONTRIBUTING.md file.
Description
The authentication glue you need.
authenticationauthentikauthorizationkubernetesoauth2oauth2-clientoauth2-serveroidcoidc-clientoidc-providerproxyreverse-proxysamlsaml-idpsaml-spsecuritysso
Readme
MIT
664 MiB
Languages
Python
51.7%
TypeScript
36.4%
MDX
5.1%
Go
3.7%
JavaScript
1.6%
Other
1.4%







