319f2ef8d1944157188c50be77bff2d1a31648d4
* web: Add InvalidationFlow to Radius Provider dialogues
## What
- Bugfix: adds the InvalidationFlow to the Radius Provider dialogues
- Repairs: `{"invalidation_flow":["This field is required."]}` message, which was *not* propagated
to the Notification.
- Nitpick: Pretties `?foo=${true}` expressions: `s/\?([^=]+)=\$\{true\}/\1/`
## Note
Yes, I know I'm going to have to do more magic when we harmonize the forms, and no, I didn't add the
Property Mappings to the wizard, and yes, I know I'm going to have pain with the *new* version of
the wizard. But this is a serious bug; you can't make Radius servers with *either* of the current
dialogues at the moment.
* This (temporary) change is needed to prevent the unit tests from failing.
\# What
\# Why
\# How
\# Designs
\# Test Steps
\# Other Notes
* Revert "This (temporary) change is needed to prevent the unit tests from failing."
This reverts commit dddde09be5.
* web/admin: allow admins to show only active users in Group assignments
## What
Adds a flag and a visible control to the "Add users to groups" dialog to limit the users
shown to only those marked as "active."
## Why
Requested, it was small, it made sense, and it was fairly trivial to implement. All the
infrastructure already existed.
## Testing
- Ensure you have both "active" and "inactive" users in your sample group.
- Visit Groups -> (One Group) -> Users ->. Click "Add existing user." Click the `+` symbol.
- A new toggle control, "Show inactive users," should now be visible.
- Click it and note whether or not the visible display corresponds to the stote of the control.
## Note
This commit does not address the second half of the request, "... the ability to add more than one
user to an entitlement." We recommend that if you have a group of people who correspond to a given
entitlement that you create a named group for them.
## Related Issue:
- [Hide disabled users when adding users to a group or entitlement
#12653](https://github.com/goauthentik/authentik/issues/12653)
* Provided an explanation for the odd expression around `CoreApi.coreUsersList:isActive`
* Use logical CSS; give room to expand
* Disambiguate variable names
core: revert bump oss/go/microsoft/golang from 1.23-fips-bookworm to 1.24-fips-bookworm (#13012) (#13022)
core: revert bump oss/go/microsoft/golang from 1.23-fips-bookworm to 1.24-fips-bookworm (#13012) (#13022)
core: revert bump oss/go/microsoft/golang from 1.23-fips-bookworm to 1.24-fips-bookworm (#13012) (#13022)
core: revert bump oss/go/microsoft/golang from 1.23-fips-bookworm to 1.24-fips-bookworm (#13012) (#13022)
core: revert bump oss/go/microsoft/golang from 1.23-fips-bookworm to 1.24-fips-bookworm (#13012) (#13022)
What is authentik?
authentik is an open-source Identity Provider that emphasizes flexibility and versatility, with support for a wide set of protocols.
Our enterprise offer can also be used as a self-hosted replacement for large-scale deployments of Okta/Auth0, Entra ID, Ping Identity, or other legacy IdPs for employees and B2B2C use.
Installation
For small/test setups it is recommended to use Docker Compose; refer to the documentation.
For bigger setups, there is a Helm Chart here. This is documented here.
Screenshots
| Light | Dark |
|---|---|
 |
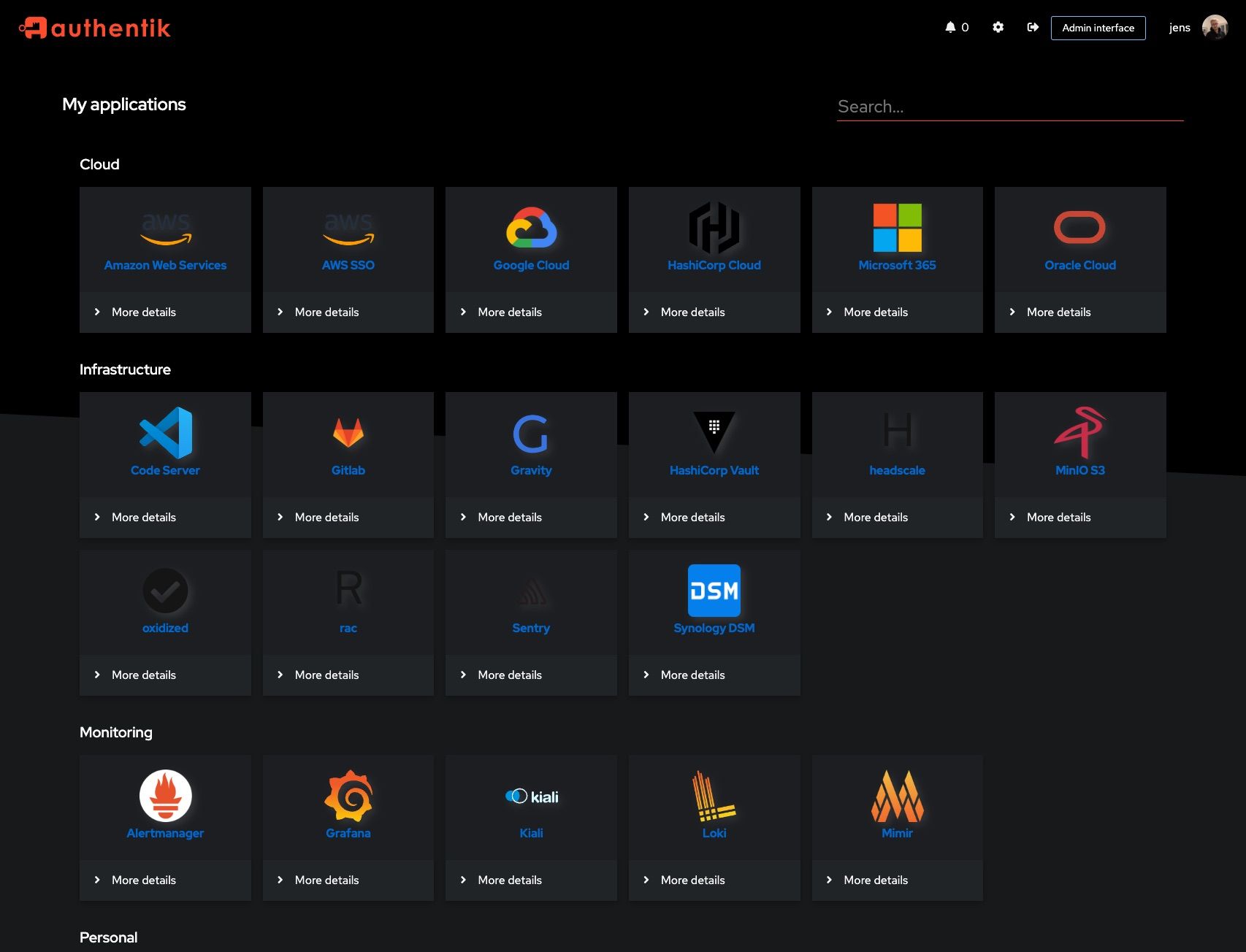 |
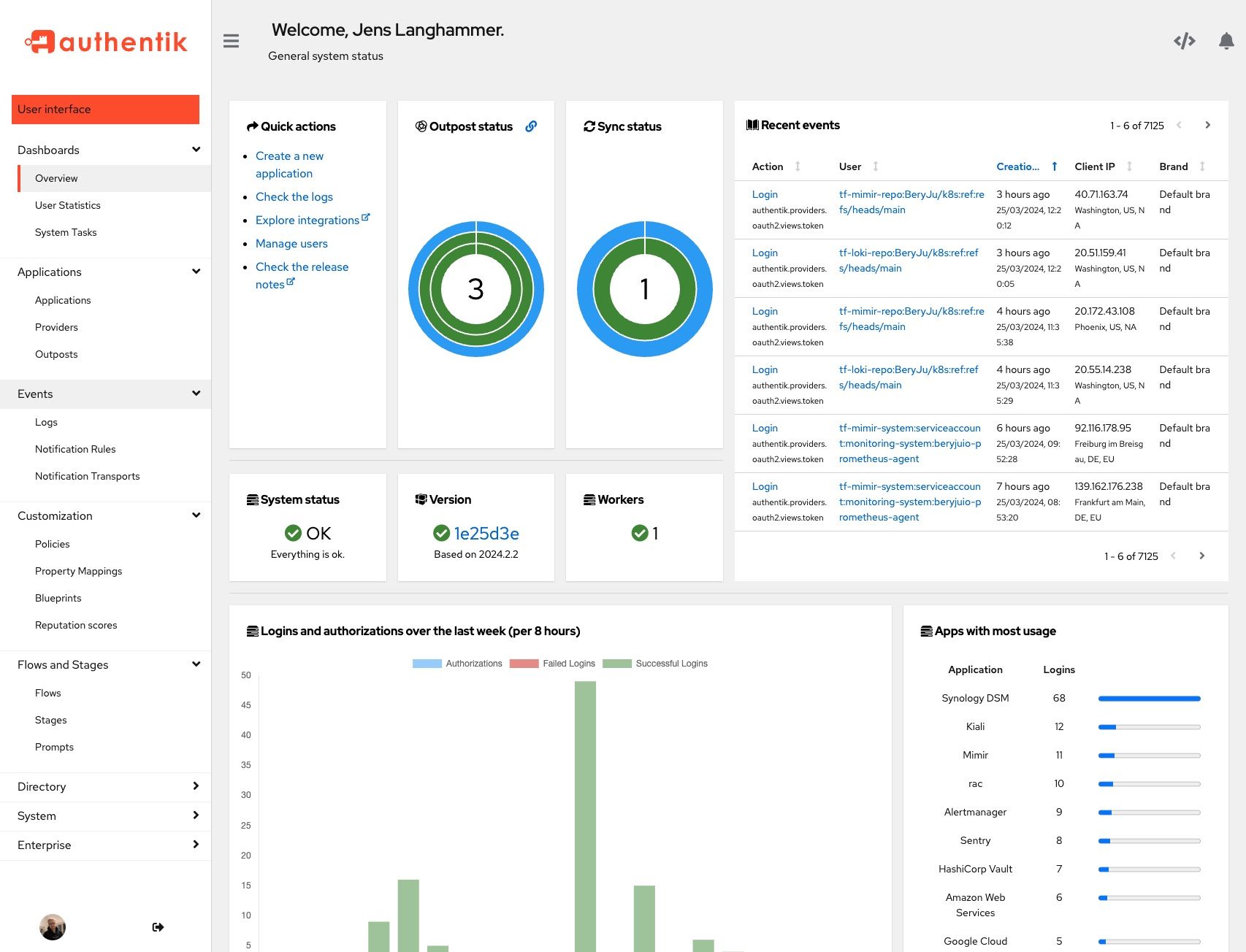 |
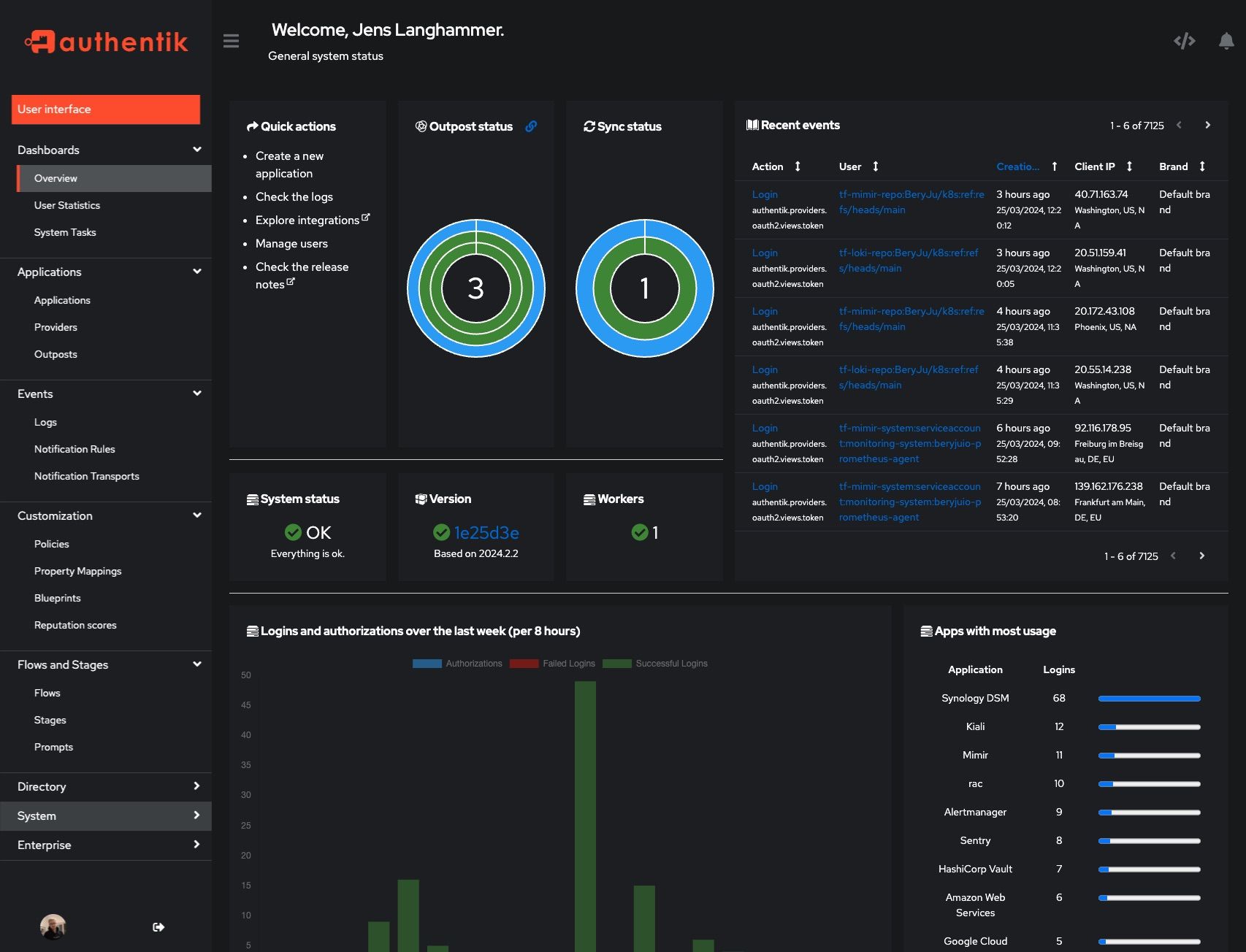 |
Development
Security
See SECURITY.md
Adoption and Contributions
Your organization uses authentik? We'd love to add your logo to the readme and our website! Email us @ hello@goauthentik.io or open a GitHub Issue/PR! For more information on how to contribute to authentik, please refer to our CONTRIBUTING.md file.
Description
The authentication glue you need.
authenticationauthentikauthorizationkubernetesoauth2oauth2-clientoauth2-serveroidcoidc-clientoidc-providerproxyreverse-proxysamlsaml-idpsaml-spsecuritysso
Readme
MIT
664 MiB
Languages
Python
51.7%
TypeScript
36.4%
MDX
5.1%
Go
3.7%
JavaScript
1.6%
Other
1.4%







