* first pass
* dependency shenanigans
* move blueprints
* few broken links
* change config the throw errors
* internal file edits
* fighting links
* remove sidebarDev
* fix subdomain
Signed-off-by: Jens Langhammer <jens@goauthentik.io>
* fix relative URL
Signed-off-by: Jens Langhammer <jens@goauthentik.io>
* fix mismatched package versions
Signed-off-by: Jens Langhammer <jens@goauthentik.io>
* fix api reference build
Signed-off-by: Jens Langhammer <jens@goauthentik.io>
* test tweak
* links hell
* more links hell
* links hell2
* yep last of the links
* last broken link fixed
* re-add cves
Signed-off-by: Jens Langhammer <jens@goauthentik.io>
* add devdocs redirects
* add dir
* tweak netlify.toml
* move latest 2 CVES into dir
* fix links to moved cves
* typoed title fix
* fix link
* remove banner
* remove committed api docs
Signed-off-by: Marc 'risson' Schmitt <marc.schmitt@risson.space>
* integrations: remove version dropdown
Signed-off-by: Marc 'risson' Schmitt <marc.schmitt@risson.space>
* Update Makefile
Signed-off-by: Marc 'risson' Schmitt <marc.schmitt@risson.space>
* change doc links in web as well
Signed-off-by: Marc 'risson' Schmitt <marc.schmitt@risson.space>
* fix some more docs paths
Signed-off-by: Marc 'risson' Schmitt <marc.schmitt@risson.space>
* fix more docs paths
Signed-off-by: Marc 'risson' Schmitt <marc.schmitt@risson.space>
* ci: require ci-web.build for merging
Signed-off-by: Marc 'risson' Schmitt <marc.schmitt@risson.space>
* Revert "ci: require ci-web.build for merging"
This reverts commit b99a4842a9.
* remove sluf for Application
* put slug back in
* minor fix to trigger deploy
* Spelled out Documentation in menu bar
* remove image redirects...
Signed-off-by: Jens Langhammer <jens@goauthentik.io>
* remove explicit index.md
Signed-off-by: Jens Langhammer <jens@goauthentik.io>
* remove mdx first
Signed-off-by: Jens Langhammer <jens@goauthentik.io>
* then remove .md
Signed-off-by: Jens Langhammer <jens@goauthentik.io>
* add missing prefix
Signed-off-by: Jens Langhammer <jens@goauthentik.io>
---------
Signed-off-by: Jens Langhammer <jens@goauthentik.io>
Signed-off-by: Marc 'risson' Schmitt <marc.schmitt@risson.space>
Co-authored-by: Tana M Berry <tana@goauthentik.com>
Co-authored-by: Jens Langhammer <jens@goauthentik.io>
Co-authored-by: Marc 'risson' Schmitt <marc.schmitt@risson.space>
3.1 KiB
title
| title |
|---|
| Github |
Support level: authentik
Allows users to authenticate using their Github credentials
Preparation
The following placeholders will be used:
authentik.companyis the FQDN of the authentik install.www.my.companyHomepage URL for your site
Github
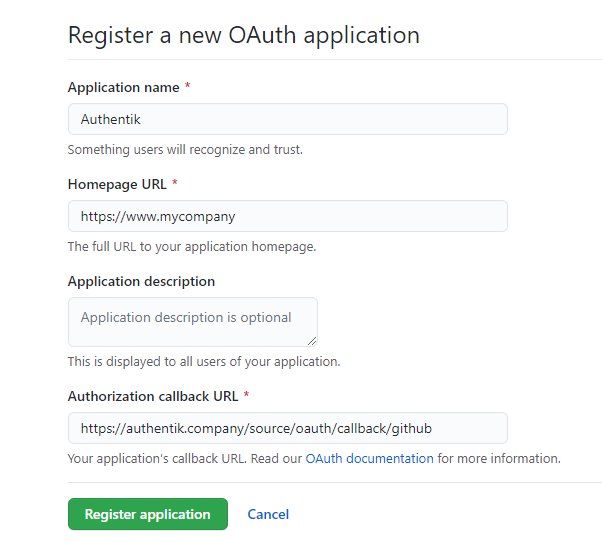
- Create an OAuth app under Developer Settings https://github.com/settings/developers by clicking on the Register a new application
- Application Name: Choose a name users will recognize ie: authentik
- Homepage URL:: www.my.company
- Authorization callback URL: https://authentik.company/source/oauth/callback/github
- Click Register Application
Example screenshot
- Copy the Client ID and save it for later
- Click Generate a new client secret and save it for later You will not be able to see the secret again, so be sure to copy it now.
authentik
-
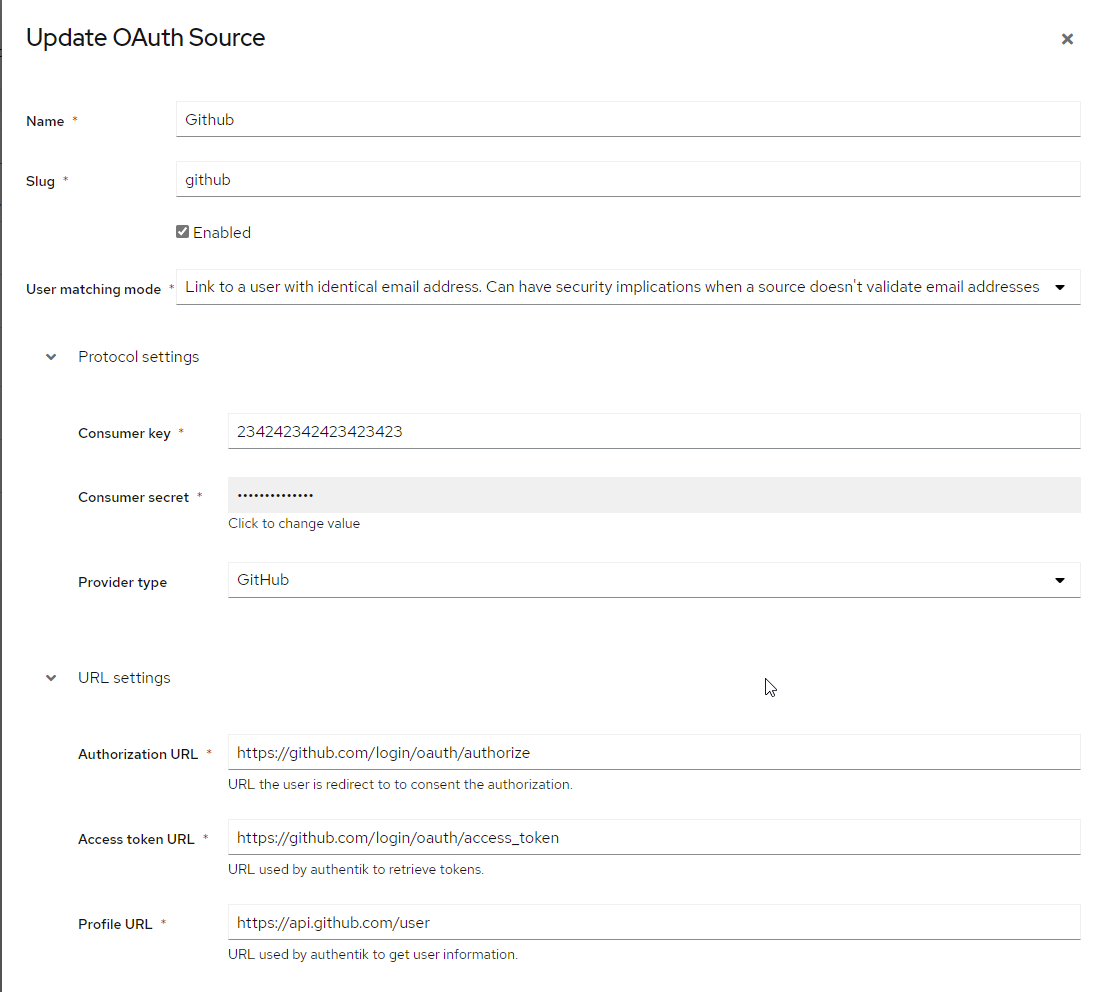
Under Directory -> Federation & Social login Click Create Github OAuth Source
-
Name: Choose a name (For the example I use Github)
-
Slug: github (If you choose a different slug the URLs will need to be updated to reflect the change)
-
Consumer Key: Client ID from step 6
-
Consumer Secret: Client Secret from step 7
Here is an example of a complete authentik Github OAuth Source
Save, and you now have Github as a source.
:::note For more details on how-to have the new source display on the Login Page see here. :::
Checking for membership of a GitHub Organisation authentik 2021.12.5.+
To check if the user is member of an organisation, you can use the following policy on your flows:
:::info
Make sure to include read:org in the sources' Scopes setting.
:::
# Ensure flow is only run during oauth logins via Github
if context["source"].provider_type != "github":
return True
accepted_org = "foo"
# Get the user-source connection object from the context, and get the access token
connection = context["goauthentik.io/sources/connection"]
access_token = connection.access_token
# We also access the user info authentik already retrieved, to get the correct username
github_username = context["oauth_userinfo"]
# Github does not include Organisations in the userinfo endpoint, so we have to call another URL
orgs_response = requests.get(
"https://api.github.com/user/orgs",
auth=(github_username["login"], access_token),
headers={
"accept": "application/vnd.github.v3+json"
}
)
orgs_response.raise_for_status()
orgs = orgs_response.json()
# `orgs` will be formatted like this
# [
# {
# "login": "goauthentik",
# [...]
# }
# ]
user_matched = any(org['login'] == accepted_org for org in orgs)
if not user_matched:
ak_message(f"User is not member of {accepted_org}.")
return user_matched
If a user is not member of the chosen organisation, they will see this message