d0217c9135e8ff2be8c127bc4dd2ac1e49b1b094
* lifecycle: install binary dependencies in dockerfile directly Signed-off-by: Jens Langhammer <jens@goauthentik.io> * install ua-parser-builtins manually as its only distributed as binary Signed-off-by: Jens Langhammer <jens@goauthentik.io> * build duo_client from scratch, sigh Signed-off-by: Jens Langhammer <jens@goauthentik.io> * deps for kadmin Signed-off-by: Jens Langhammer <jens@goauthentik.io> * ok fine Signed-off-by: Jens Langhammer <jens@goauthentik.io> * run on arm runner? Signed-off-by: Jens Langhammer <jens@goauthentik.io> * fix yaml format Signed-off-by: Jens Langhammer <jens@goauthentik.io> * rewrite release pipeline to use re-usable workflows Signed-off-by: Jens Langhammer <jens@goauthentik.io> * fix typo Signed-off-by: Jens Langhammer <jens@goauthentik.io> * re-usable multi-arch build? Signed-off-by: Jens Langhammer <jens@goauthentik.io> * also add suffix for amd64 Signed-off-by: Jens Langhammer <jens@goauthentik.io> * parameterise image name Signed-off-by: Jens Langhammer <jens@goauthentik.io> * re-use workflow for CI images...? Signed-off-by: Jens Langhammer <jens@goauthentik.io> * fix missing checkout Signed-off-by: Jens Langhammer <jens@goauthentik.io> * inherit secrets Signed-off-by: Jens Langhammer <jens@goauthentik.io> * temp build directly Signed-off-by: Jens Langhammer <jens@goauthentik.io> * get cache-to from python script Signed-off-by: Jens Langhammer <jens@goauthentik.io> * better name? Signed-off-by: Jens Langhammer <jens@goauthentik.io> * matrix for merging images? Signed-off-by: Jens Langhammer <jens@goauthentik.io> * re-add build dep Signed-off-by: Jens Langhammer <jens@goauthentik.io> * use multi-image tag Signed-off-by: Jens Langhammer <jens@goauthentik.io> * include arch in buildcache Signed-off-by: Jens Langhammer <jens@goauthentik.io> --------- Signed-off-by: Jens Langhammer <jens@goauthentik.io> # Conflicts: # .github/workflows/ci-main.yml # .github/workflows/release-publish.yml
What is authentik?
authentik is an open-source Identity Provider that emphasizes flexibility and versatility, with support for a wide set of protocols.
Our enterprise offer can also be used as a self-hosted replacement for large-scale deployments of Okta/Auth0, Entra ID, Ping Identity, or other legacy IdPs for employees and B2B2C use.
Installation
For small/test setups it is recommended to use Docker Compose; refer to the documentation.
For bigger setups, there is a Helm Chart here. This is documented here.
Screenshots
| Light | Dark |
|---|---|
 |
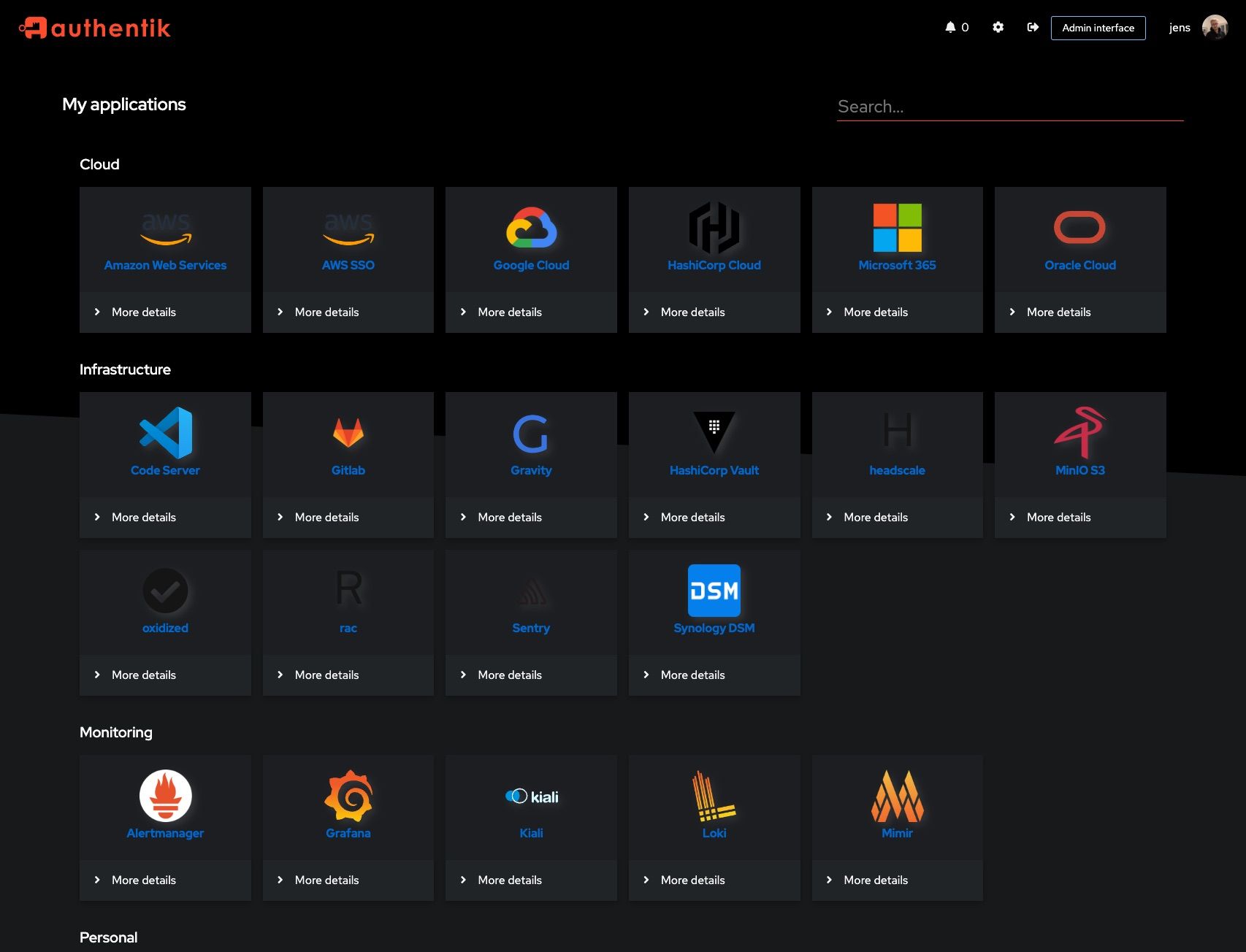 |
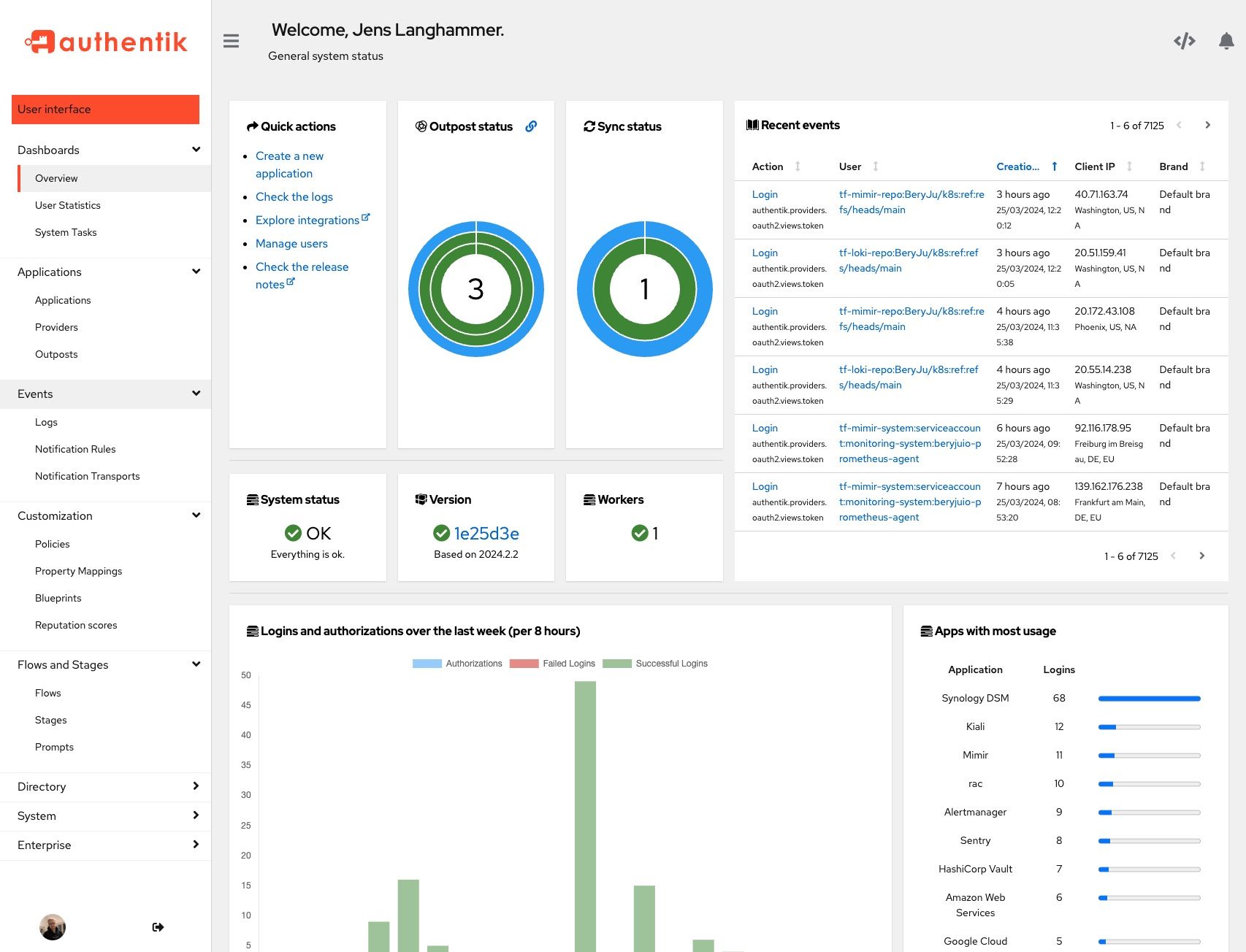 |
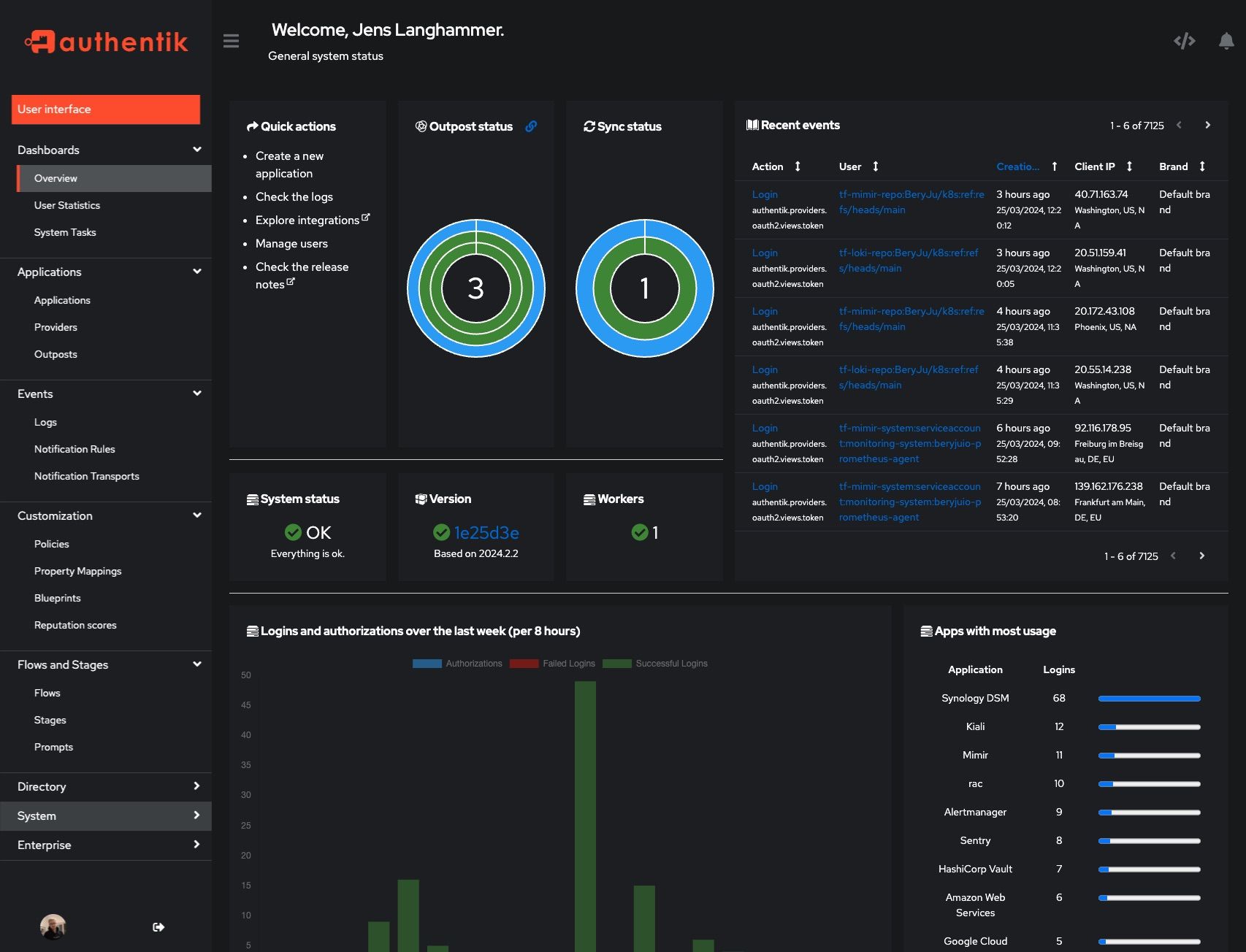 |
Development
Security
See SECURITY.md
Adoption and Contributions
Your organization uses authentik? We'd love to add your logo to the readme and our website! Email us @ hello@goauthentik.io or open a GitHub Issue/PR! For more information on how to contribute to authentik, please refer to our CONTRIBUTING.md file.
Description
The authentication glue you need.
authenticationauthentikauthorizationkubernetesoauth2oauth2-clientoauth2-serveroidcoidc-clientoidc-providerproxyreverse-proxysamlsaml-idpsaml-spsecuritysso
Readme
MIT
664 MiB
Languages
Python
51.7%
TypeScript
36.4%
MDX
5.1%
Go
3.7%
JavaScript
1.6%
Other
1.4%







