fb2401cf9e9702da1d9cf553ce36c23c14065932
* Update Zammad SAML Instructions I just configured Zammad 6.4.1 to work with Authentik 2025.4.1. There seem to have been some changes since these instructions were written. The Name ID Format cannot be left blank. The SSO URL and the logout URL were incorrect. I was getting an Error 422 from Zammad until I turned on signing assertions, so I conclude that is required and I wrote instructions for that. I saw some discussion online elsewhere that the `----BEGIN` and `---END` lines should be removed. I tested it both ways and it worked both ways. I wrote the instructions to keep those lines in because it seemed simplest and most intuitive. Signed-off-by: Paco Hope <pacohope@users.noreply.github.com> * Incorporate separate instructions for certificate file Co-authored-by: Dewi Roberts <dewi@goauthentik.io> Signed-off-by: Paco Hope <pacohope@users.noreply.github.com> * Incorporate simplified copy/paste instructions Co-authored-by: Dewi Roberts <dewi@goauthentik.io> Signed-off-by: Paco Hope <pacohope@users.noreply.github.com> * Incoporate formatting change Co-authored-by: Dewi Roberts <dewi@goauthentik.io> Signed-off-by: Paco Hope <pacohope@users.noreply.github.com> * Incorporate formatting changes Co-authored-by: Dewi Roberts <dewi@goauthentik.io> Signed-off-by: Paco Hope <pacohope@users.noreply.github.com> * Removed reference to custom properties * Capitalisation Co-authored-by: Dominic R <dominic@sdko.org> Signed-off-by: Paco Hope <pacohope@users.noreply.github.com> * Formatting Co-authored-by: Dominic R <dominic@sdko.org> Signed-off-by: Paco Hope <pacohope@users.noreply.github.com> * Formatting Co-authored-by: Dominic R <dominic@sdko.org> Signed-off-by: Paco Hope <pacohope@users.noreply.github.com> * Updated language Co-authored-by: Dominic R <dominic@sdko.org> Signed-off-by: Paco Hope <pacohope@users.noreply.github.com> * Update website/integrations/services/zammad/index.md Co-authored-by: Dominic R <dominic@sdko.org> Signed-off-by: Paco Hope <pacohope@users.noreply.github.com> * Update website/integrations/services/zammad/index.md Co-authored-by: Dominic R <dominic@sdko.org> Signed-off-by: Paco Hope <pacohope@users.noreply.github.com> * tweak to bump build * bump build * use bold font for UI labels * my typo * capitalization fix --------- Signed-off-by: Paco Hope <pacohope@users.noreply.github.com> Co-authored-by: Dewi Roberts <dewi@goauthentik.io> Co-authored-by: Dominic R <dominic@sdko.org> Co-authored-by: Tana M Berry <tana@goauthentik.io>
web: bump @sentry/browser from 9.22.0 to 9.23.0 in /web in the sentry group across 1 directory (#14776)
What is authentik?
authentik is an open-source Identity Provider that emphasizes flexibility and versatility, with support for a wide set of protocols.
Our enterprise offer can also be used as a self-hosted replacement for large-scale deployments of Okta/Auth0, Entra ID, Ping Identity, or other legacy IdPs for employees and B2B2C use.
Installation
For small/test setups it is recommended to use Docker Compose; refer to the documentation.
For bigger setups, there is a Helm Chart here. This is documented here.
Screenshots
| Light | Dark |
|---|---|
 |
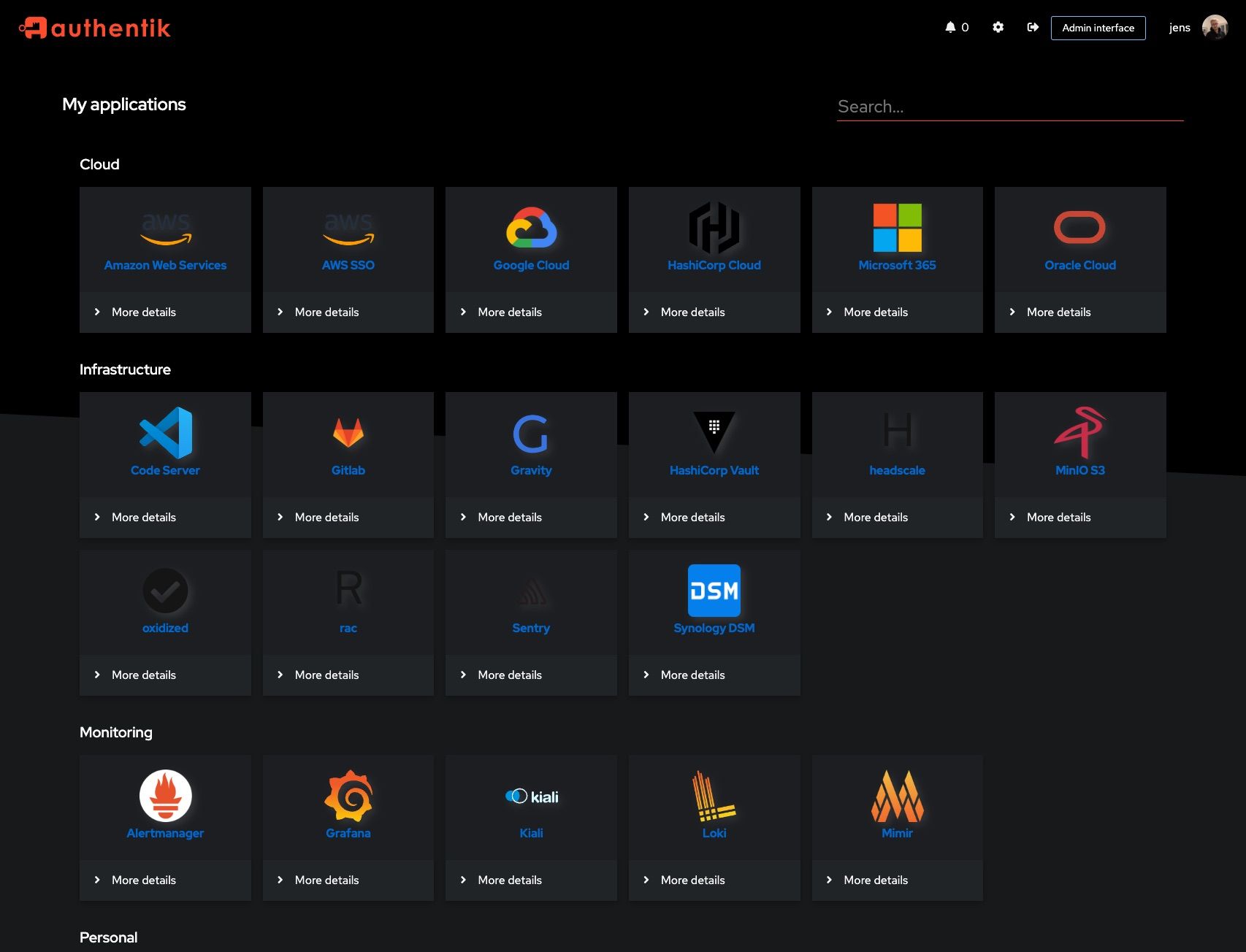 |
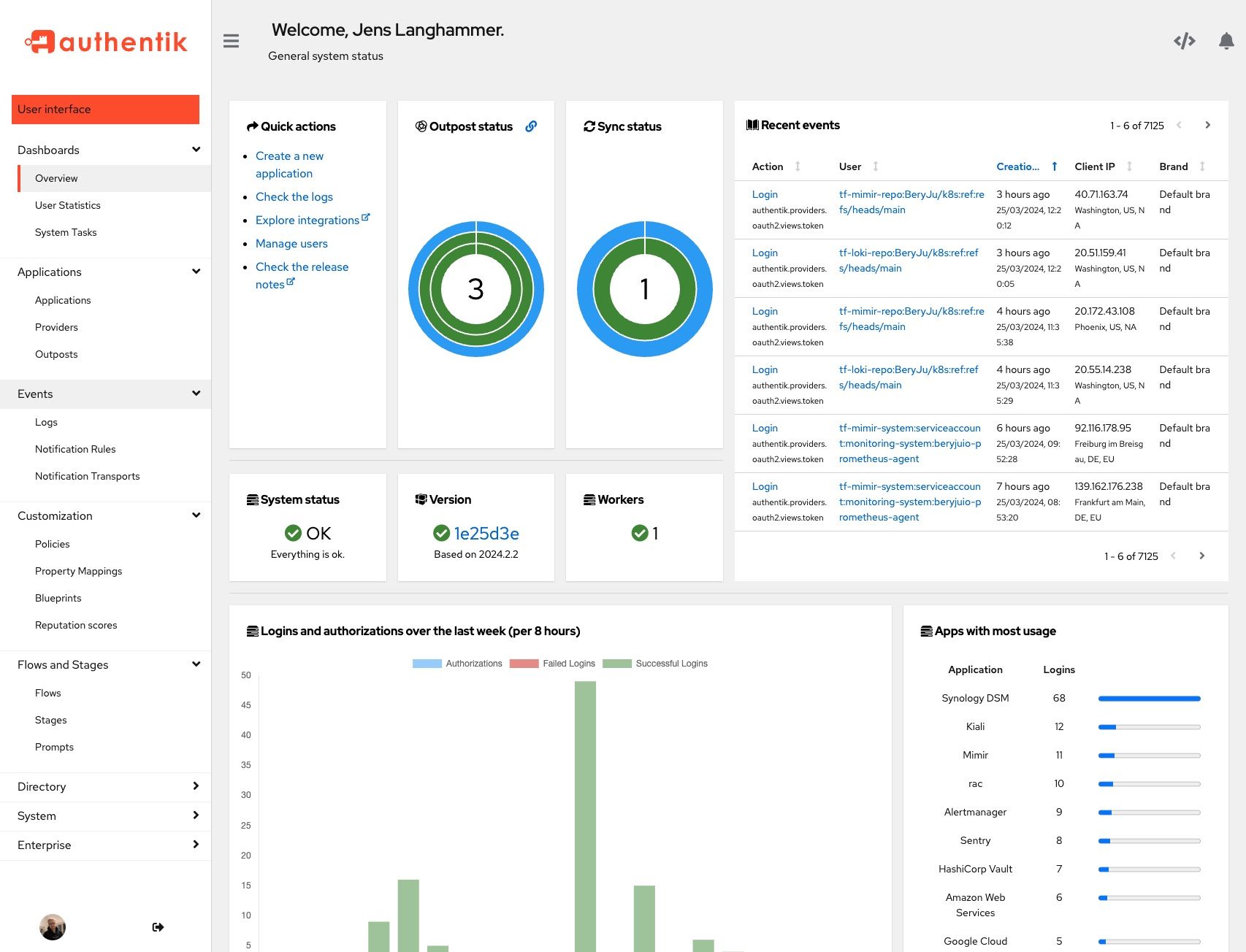 |
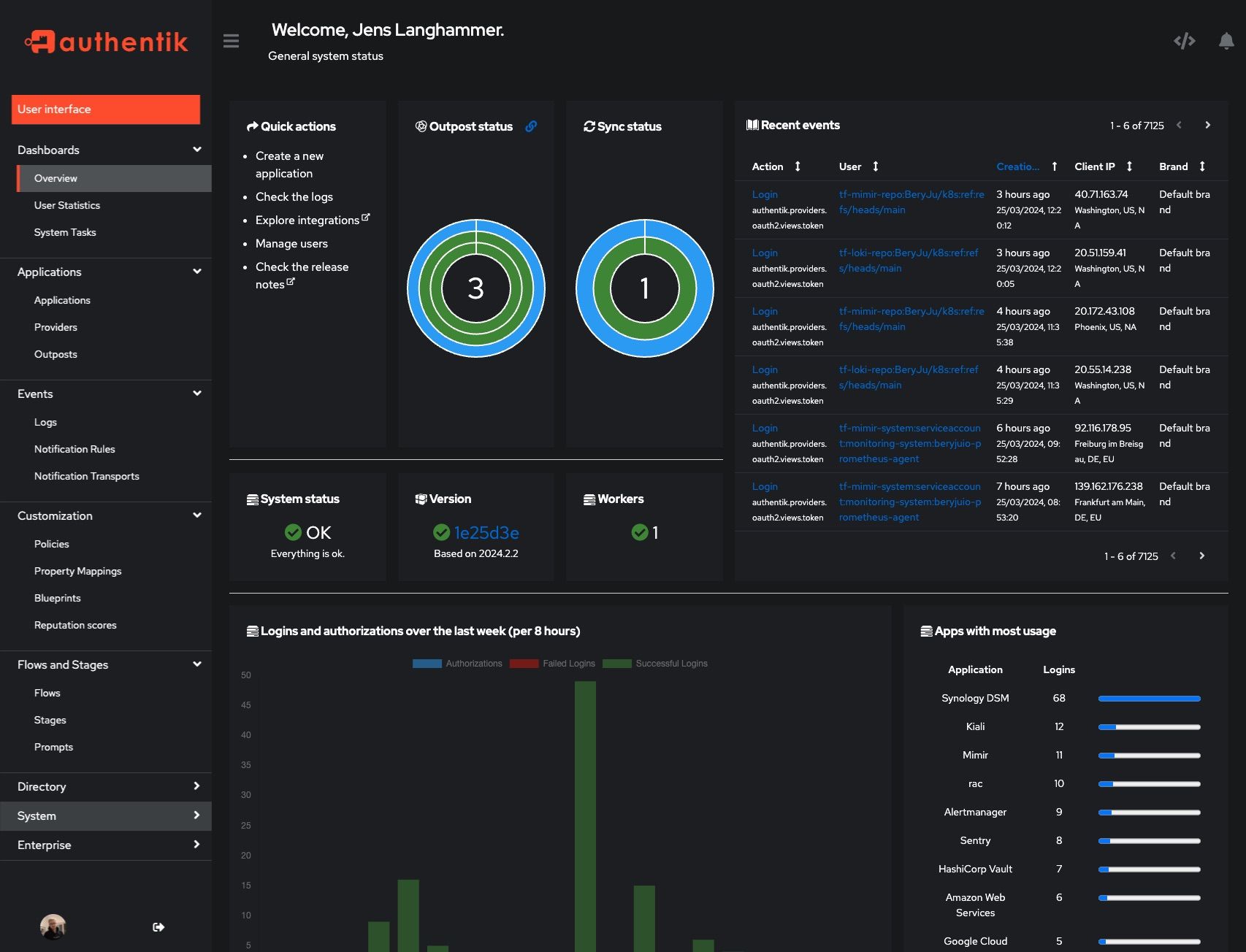 |
Development
Security
See SECURITY.md
Adoption and Contributions
Your organization uses authentik? We'd love to add your logo to the readme and our website! Email us @ hello@goauthentik.io or open a GitHub Issue/PR! For more information on how to contribute to authentik, please refer to our contribution guide.
Description
The authentication glue you need.
authenticationauthentikauthorizationkubernetesoauth2oauth2-clientoauth2-serveroidcoidc-clientoidc-providerproxyreverse-proxysamlsaml-idpsaml-spsecuritysso
Readme
MIT
664 MiB
Languages
Python
51.7%
TypeScript
36.4%
MDX
5.1%
Go
3.7%
JavaScript
1.6%
Other
1.4%







